A Private Affair
We are nearing the end of the memoir. We have touched upon most of the fundamentals of this technology, and you might feel that you are ready to explore blockchain in detail. So before you start, here is a fair bit of warning.
So far, throughout the memoir, we talked about how blockchain is a completely decentralized system with copies of the data made available to everyone in the network. But when you look at that statement from a practical sense, it does hold some problem. Suppose we create a blockchain application for wholesale business. The wholesaler has multiple clients, and he uses the application to sell products to his retail customers. Now, it might be a sound business strategy to provide discounts to particular customers to keep business relations alive. He might sell products at a different price to different individuals. It is a common yet covert practice. Now, since we are building a blockchain application for managing the business, it makes this kind of information publicly available for everyone, meaning a buyer can see the price at which the product is sold to a different buyer. The above scenario can pose some problems to the wholesaler’s establishment.
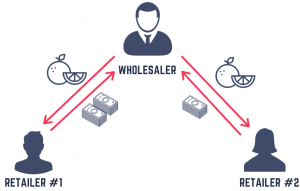
The takeaway from this example is that most business applications require a certain amount of data confidentiality. Not every business application requires the data to be made public. This is where the concept of permissioned blockchains comes in. A permissioned blockchain retains all the basic properties of a public blockchain, plus, it allows the user to control access to the information. In a permissioned blockchain, we can give access permissions ( both read and write) to users based on a variety of factors. This enables the users to retain control over the data and maintain the desired level of data confidentiality.
To recap, there are two kinds of blockchains ( broadly speaking). A public blockchain allowing the information in the chain to be made public to any participant in the network and a permissioned blockchain allowing access control over the data. Both the public and permissioned chains have their specific use cases. As aspiring developers, you have to figure out the type of chain that fits a particular use case.