Chain Effect – Illustrated
The digital ledger contains the current state of a business as a journal of transactions. For instance, looking at our bank statement, we would be able to identify the set of transactions (credit and debit) related to our account, and from these transactions, we could derive the current state (balance) of the account. It is not just the financial transactions that we can record in a ledger, it enables recordings of contracts, payments, buy-sell deals, movement of assets, or property.
Let’s try to understand how a typical vehicle registration process is performed.
If a person wishes to own a car, it is inevitable to go through certain processes associated with purchase and registration. When a car is bought, the car dealer can help to do the registration for the buyer in exchange for a certain price. Once the documents have been verified by the RTO, the car will get registered under the buyer’s credentials.
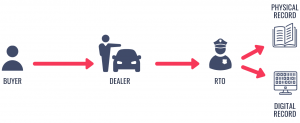
The details of the registration are recorded in ledgers. Nowadays, modern governments use digital ledger for record-keeping, but even now some countries rely on physical ledger books for the same. We believe that our records are safe and secure since it is controlled by a government institution. But what prevents someone from tampering with the data and removing our entry from the ledger book? Can they also edit the registration details which are stored digitally? How could we prove the ownership of the vehicle to a third party without the help of a centralized authority?
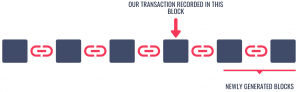
Let’s assume that whenever someone buys a new vehicle, the transaction is recorded into a block in the blockchain.

More blocks will get added to this chain over time since new transactions happen frequently.
If a malicious group wants to tamper with our data, they have to first edit the block where the details are stored. A change in the data would lead to a change in the hash value of the block, which in turn breaks the cryptographic link between the blocks.
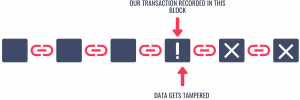
To make this chain valid again, they have to recreate the cryptographic link by calculating the hash of each block. This is a time-consuming process. If we have stored the chain in a single computer then an attacker would be able to update the chain by following the time-consuming process. To avoid this problem, we can replicate the ledger onto multiple machines. This would force the attacker to do an update on the chain present in multiple machines which is practically impossible.
Thus we could say that it is practically impossible for an attacker to update the ledger or blockchain, which is why we call them Immutable Ledger.
So far we talked about how a decentralized, distributed digital ledger technology stores details of the transaction in an immutable way. But how do we perform these transactions? If there are no third parties involved, who conducts these transactions?