Chaining the blocks !
In the last section, we talked about hash values, now let’s look at how we can create a chain out of these hash values.
Imagine a block in a blockchain. The first part of the “chaining” process involves the generation of the hash value for that particular block. To do this, we take all the available data in the block (from the block header as well as the body) and pass it through a hash function. This provides the hash value of the current block. This is the value that we store in the current hash field in the block header. Next, the current hash of the block is passed on to the next block, where it is stored as the previous hash (in the previous hash field in its header). This means that along with its hash value, any given block in a blockchain will contain the hash value of its previous block. Every block repeats the process and passes its current hash to the next block. This process “links or chains” the blocks in a blockchain to its previous blocks. The ‘previous hash value field of a genesis block (block-0) is either empty or filled with zeros as there is no previous block for a Genesis block.
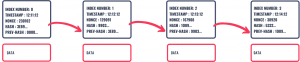
You might ask what benefit do we acquire via chaining? Well, since the blocks are cryptographically linked using hash values, any change in the ‘data’ stored in a block would result in a change in the hash value of the block, and this will invalidate the current hash of this particular block and the previous hash of the subsequent block. This will end up “breaking” the whole blockchain. So, the cryptographic links make sure that the data, once entered into the blockchain, remains tamper-resistant. This makes blockchain a decentralized, distributed, digital, and immutable ledger technology.