Hashing It Out !
Let’s see the components inside the header part of a block. There are two fields called the previous and current hash. To understand the “chaining” part of a blockchain, we must look into these fields. The previous and current hash fields contain something called the hash value. While the current hash field contains the hash value of the current block, the previous hash field contains the hash value of the previous block. A hash value is a unique value that helps us identify a piece of information. In cryptography, we use something called the hashing algorithm to generate these hash values.
To better understand the principle of hashing in cryptography, let’s first try to understand how human fingerprints work.
It has been identified that human fingerprints are unique. It is now possible to identify the owner of a fingerprint through forensic methods. The chances of fingerprint collision (two people having the same fingerprint) are too low (1 in 60 million). So, it is safe to assume that each person has a unique fingerprint.
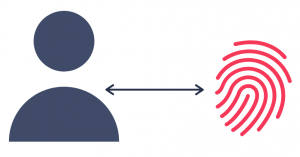
In the digital world, we have a similar principle called the hash value, which is like a fingerprint (identifier) of data. The generation of the hash value is done by a hashing algorithm. Just like the fingerprint, a particular hash value can only be generated by a particular piece of data. Even the minute change in the data will result in an entirely different hash value.
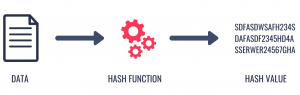
The hashing algorithm has certain characteristics. It is a one-way function, which means it is not possible to recreate the data or documents from a given hash value. It can withstand collisions, meaning, it is highly unlikely that two pieces of data will produce the same hash. The value produced by a hash algorithm will always be of the same length and size, no matter the size of the input data.
So how does the hash value help in chaining the blocks?